GMAT Prep 20242025 for Dummies - Practice Test
Section 1: Data Insights
TIME: 45 minutes for 20 questions
DIRECTIONS: [For the 20 data insights questions, follow the directions provided in online Practice Test 1.]
Section 2: Quantitative
TIME: 45 minutes for 21 questions
DIRECTIONS: Choose the best answer from the five choices provided.
(10xy + 15x)/(2y + 3) + 3y = 1
1. If x = 4 and y ≠ -1.5, what is the value of y?
(A) -19/3
(B) -3/19
(C) 3/19
(D) 1/3
(E) 19/3
2. A stand at a farmer’s market is selling peaches individually and in cartons. An individual peach costs $1. When bought in a carton of 30, the price of each peach is discounted by 10 percent. Since it is the end of the growing season, there is a sale going on where the price is further discounted by 60 percent. What is the price of two cartons of peaches?
(A) $9.00
(B) $10.80
(C) $18.00
(D) $21.60
(E) $32.40
3. The table shows the peak price each year for stocks from five different companies. Which stock had the greatest increase in peak price from Year 1 to Year 3?
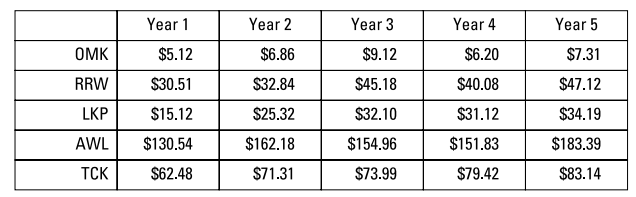
(A) OMK
(B) RRW
(C) LKP
(D) AWL
(E) TCK
4. If y = 1, what is the value of the following expression: (4y+z)(16)(4-z)?
(A) 4
(B) 16
(C) 64
(D) 128
(E) 256
5. When x ≠ 0, (2/x +1/3)(x/2) can be simplified to which one of the following?
(A) 1 + x/6
(B) (3x - 2)/3
(C) 1/6 + x
(D) 1/3
(E) 3x/(2x + 6)
6. If x - y = 8 and 5x + y = -8, then x + y =
(A) -2
(B) -8
(C) 2
(D) 3
(E) 8
7. If y = x/2 and x ≠ 0, which one of the following is equal to y/2x + x/4?
(A) (4x2 + x)/4
(B) (x + 1)/4
(C) (x + 4)/2x
(D) x2 + 1
(E) 1/4
8. Anthony runs a business manufacturing machine parts. If Anthony’s business manufactured 80,000 machine parts last year and 88,000 machine parts this year, how many parts must the business produce next year to maintain the same percent growth from year to year?
(A) 88,000
(B) 88,800
(C) 96,000
(D) 96,800
(E) 100,000
9. Patrick and Mel are each selling shirts at a rock concert to promote their favorite bands. It costs each of them the same amount to produce each shirt. Mel is selling her shirts for $60. If Patrick is making 20 percent more profit than Mel, and his profit is $24 per shirt, how much is Patrick charging for his shirts?
(A) $48.00
(B) $62.00
(C) $64.00
(D) $68.80
(E) $72.00
10. If 7(x/2 + x/5) = 3, what is the value of x?
(A) 3/49
(B) 30/49
(C) 30/49
(D) 15/7
(E) 49/3
11. Given (3 - 5x)/2 + 4 < (x + 2)/3, which one of the following describes the possible values for x?
(A) x < 29/17
(B) x < 3/14
(C) x < -29/17
(D) x > 29/17
(E) x > 1/6
12. A parking lot contains ten cars. The average age of the cars is seven years. If the average age of nine of the cars is six years, what is the age of the remaining car in years?
(A) 3
(B) 7
(C) 10
(D) 16
(E) 20
13. If Cindy ran at 7.5 miles per hour for 16 minutes, and then ran at 6 miles per hour for 10 minutes, how far in miles did she run in total?
(A) 2.5
(B) 2.8
(C) 3
(D) 3.5
(E) 5
14. If x > 0 and 2x2 - 81 = 0, what is the value of x?
(A) 4.5
(B) 6
(C) √40.5
(D) √45
(E) √162
15. Taco Fusion restaurant served a total of 60 guests for lunch today. Twenty of the guests ordered sushi, and 45 of the guests ordered tacos. If five of the guests didn’t order tacos or sushi, how many of the guests ordered both?
(A) 0
(B) 5
(C) 10
(D) 15
(E) 20
16. A flag football league has ten teams. Each game in the season is between two teams from the league. If each team plays each of the other teams exactly one time, how many games are played in a season?
(A) 20
(B) 45
(C) 50
(D) 90
(E) 100
17. If one seedling grew 6 inches, while a second seedling grew 250 percent more than the first, how many inches did the second seedling grow?
(A) 6
(B) 8
(C) 12
(D) 15
(E) 21
18. Identify which one of the following expressions can be simplified to a rational number?
I. (√46√46)/(46)2
II. (√46 + √46)2
III. 46√46
(A) I only
(B) II only
(C) III only
(D) I and II only
(E) II and III only
19. The number of red dots is 4 times the number of blue dots, which, in turn is twice the number of yellow dots. What is the ratio of the number of red dots to the number of yellow dots?
(A) 8:1
(B) 4:1
(C) 1:2
(D) 1:4
(E) 1:8
20. The simultaneous solution of (2x + 1)(4x - 1) = 0 and (5x - 1)(x - 1/4) = 0 is x =
(A) -1/2
(B) -1/4
(C) 1/5
(D) 1/4
(E) 1/2
21. The range of the six numbers, 20, 6, 14, 8, 28, and N is 24. What is the difference between the greatest and least possible values of N?
(A) 4
(B) 24
(C) 26
(D) 30
(E) 34
Section 3: Verbal
TIME: 45 minutes for 23 questions
DIRECTIONS: Follow these directions for each of the two question types:
• Reading comprehension questions: Choose the best answer to every question based on what the passage states directly or indirectly.
• Critical reasoning questions: Pick the answer choice that best answers the question about the argument provided.
Questions 1–6 refer to the following passage, which is excerpted from Playing against Nature: Integrating Science and Economics to Mitigate Natural Hazards in an Uncertain World, by Seth Stein and Jerome Stein (John Wiley & Sons, Inc. 2014).
Natural hazards are the price we pay for living on an active planet. The tectonic plate subduction producing Japan’s rugged Tohoku coast gives rise to earthquakes and tsunamis. Florida’s warm sunny weather results from the processes in the ocean and atmosphere that cause hurricanes. The volcanoes that produced Hawaii’s spectacular islands sometimes threaten people. Rivers that provide the water for the farms that feed us sometimes flood.
Humans have to live with natural hazards. We describe this challenge in terms of hazards, the natural occurrence of earthquakes or other phenomena, and the risks, or dangers they pose to lives and property. In this formulation, the risk is the product of hazard and vulnerability. We want to assess the hazards — estimate how significant they are — and develop methods to mitigate or reduce the resulting losses.
Hazards are geological facts that are not under human control. All we can do is try to assess them as best we can. In contrast, risks are affected by human actions that increase or decrease vulnerability, such as where people live and how they build. We increase vulnerability by building in hazardous areas, and decrease it by making buildings more hazard resistant. Areas with high hazard can have low risk because few people live there. Areas of modest hazard can have high risk due to large population and poor construction. A disaster occurs when — owing to high vulnerability — a natural event has major consequences for society.
The harm from natural disasters is enormous. On average, about 100,000 people per year are killed by natural disasters, with some disasters — such as the 2004 Indian Ocean tsunami — causing many more deaths. Although the actual numbers of deaths in many events, such as the 2010 Haiti earthquake, are poorly known, they are very large.
Economic impacts are even harder to quantify, and various measures are used to try to do so. Disasters cause losses, which are the total negative economic impact. These include direct losses due to destruction of physical assets such as buildings, farmland, forests, etc., and indirect losses that result from the direct losses. Because losses are hard to determine, what is reported is often the cost, which refers to payouts by insurers (called insured losses) or governments to reimburse some of the losses. Thus, the reported cost does not reflect the losses to people who do not receive such payments.
1. The main idea of the first paragraph is best expressed as
(A) the factors that make an area desirable are also those that can pose the most risk.
(B) the Hawaiian Islands would not exist if not for powerful and explosive volcanoes.
(C) floods, volcanoes, and earthquakes pose threats to the natural environment.
(D) humans must learn to live with natural hazards such as volcanoes and tsunamis.
(E) natural hazards are most prevalent in areas that are sunny and warm.
2. Which one of the following might the author of the passage consider an “indirect loss” associated with a disaster?
(A) Desecration of a library due to vandalism
(B) Damage to a school building in a fire
(C) Loss of retail clothing sales due to a mall flood
(D) Death of a ranch’s livestock due to a volcanic eruption
(E) Destruction of a pavilion due to a hurricane
3. According to the passage, an important distinction between hazards and risks is
(A) risks occur naturally, while hazards arise because of human actions.
(B) hazards result from risks, and risks result from vulnerability.
(C) hazards can lead to disasters, while risks cannot.
(D) hazards are not under human control, while risks usually are.
(E) risks are harder to quantify than hazards.
4. The passage is primarily concerned with
(A) describing the causes and impacts of natural disasters.
(B) assessing the impact that disasters render on the global economy.
(C) depicting the various ways human beings may endanger themselves.
(D) raising awareness of the loss of human lives due to the severity and unpredictability of natural disasters.
(E) explaining that natural disasters are not under human control.
5. Which one of the following best describes the purpose of the fourth paragraph in relation to the passage as a whole?
(A) It uses numerical data and metrics to describe the economic impacts of natural disasters.
(B) It emphasizes how little is known about how many lives are lost in natural disasters.
(C) It outlines the differences between hazards and risks to set up information detailed in the remainder of the passage.
(D) It provides sensory details about specific recent natural disasters that may be familiar to readers to evoke an emotional response.
(E) It applies statistical data to emphasize the magnitude of damage created by natural disasters.
6. Which one of the following logically follows the information given in the passage?
(A) The number of unreported deaths in the 2010 Haitian earthquake exceeded the number of unreported deaths in the 2004 Indian Ocean tsunami.
(B) In the years 2010 and 2004, there were more deaths than average due to natural disasters.
(C) The number of deaths due to natural disasters along Japan’s tectonic plate is greater on average than those experienced on islands such as Hawaii or Haiti.
(D) Economic costs are more frequently unreported than numbers of deaths in any given natural disaster.
(E) Areas of high hazard, such as Japan’s Tohoku coast, may have a lower risk of natural disaster costs than areas where hazard incidents are lower.
7. The size of oceanic waves is a function of the velocity of the wind and of fetch, the length of the surface of the water subject to those winds. The impact of waves against a coastline is a function of the size of the waves and the shape of the sea bottom. The degree of erosion to which a coastline is subject is a function of the average impact of waves and the geologic composition of the coastline.
If these statements are true, which one of the following must also be true?
(A) The degree of erosion to which a coastline is subject is related to the shape of the sea bottom.
(B) The size of oceanic waves will not fluctuate far from an average for any given stretch of ocean.
(C) The fetch of winds is related to the shape of the sea bottom.
(D) The size of oceanic waves is related to the shape of the sea bottom.
(E) The average velocity of the wind in an area plays no role in the degree of erosion to which a coastline is subject.
8. Health insurers are largely immune to the factors that are limiting profit in many sectors of the healthcare economy. Consumers have shown a willingness to pay almost any price for health insurance premiums. Capital demands, which are the responsibility of doctors and hospitals, are increasing dramatically, even as cost-containment measures, largely encouraged by the insurers and their friends in government, have forced new levels of fiscal discipline upon hospitals and doctors. Patients still need MRI scans and buildings to conduct them in, but hospitals are limited in how much they can charge patients for the use of these facilities.
Which one of the following most accurately describes the role that the statement “patients still need MRI scans and buildings to conduct them in” plays in the argument?
(A) It is a specific example of a general condition described during the argument.
(B) It is used to counter a consideration that may be taken to undermine the argument.
(C) It is used to indirectly support the claim made by the argument.
(D) It describes a social side effect of the benefit with which the argument is concerned.
(E) It introduces the conclusion that the argument intends to support.
9. Forcing businesses to furnish employees with paid leave for family concerns, such as family leave or leave to care for a sick child, is a terrible idea. If a business allows employees to take this time off, the workers will take advantage of the privilege and come to work as little as possible. This will destroy productivity and workplace morale.
Which one of the following, if true, most seriously weakens the argument?
(A) European countries guarantee employees generous family leave and paid vacation time, but the European standard of living is slightly below that of the United States.
(B) Most male workers refuse to take family leave even though it is allowed under federal law and their employers encourage it; they fear they may anger co-workers and harm their chances for promotion if they take time off for what is still seen as a frivolous reason.
(C) The Family and Medical Leave Act requires employers to grant employees 12 weeks a year of unpaid leave for family purposes; although employers save money because the leave is unpaid, they often must spend money to find a replacement for the employee who takes time off.
(D) In some workplaces, the loss of a single employee at a busy time of year can be devastating, even if that employee plans to return after a few weeks; allowing family leave can overwhelm the employees who stay on the job.
(E) Allowing employees to take leave for family matters reduces absenteeism, improves morale, and surprisingly increases productivity because the employees who are granted leave tend to work much harder and more efficiently when they come back to work.
10. Software engineers know that a poorly written application can consume more memory than it should and that running out of memory can cause an application to crash. However, if a crashing application causes the whole operating system to crash, the fault lies with the operating system.
Which one of the following, if true, is least helpful in establishing that this conclusion is properly drawn?
(A) Operating systems with generous amounts of memory are less susceptible to crashing, even when applications are poorly written.
(B) Operating systems can isolate the memory used by individual applications, even when an application uses a large amount of memory.
(C) An operating system can monitor an application’s consumption of memory and act when that consumption gets too high.
(D) Techniques for programming operating systems to catch and manage memory errors are well defined and well known among programmers.
(E) Because many applications can run simultaneously under a single operating system, the operating system should have a well-defined method of managing memory consumption.
11. This museum does not grant people the right to use images of items in its collection in online publications. We are obliged to do everything in our power to ensure the continued appeal of visiting our collection in person.
The above conclusion depends on assuming which one of the following?
(A) Taking photographs of art objects, especially using a flash, can damage the objects by accelerating the fading of paint.
(B) The museum sells pictures of its collection in its gift shop, which is an important source of income for the museum.
(C) Images placed online are easily copied and reused by other people.
(D) The quality of most electronic images, especially those online, falls short of the professional standards of the museum.
(E) If people see online images of items in the museum’s collection, they will no longer be interested in seeing the collection with their own eyes.
Questions 12–15 refer to the following passage, which is excerpted from Handbook of Early Childhood Development Programs, Practices, and Policies, by Elizabeth Votruba-Drzal (Editor) and Eric Dearing (Editor) (John Wiley & Sons, Inc. 2017).
Researchers, educators, and policymakers generally agree that school readiness is a multidimensional concept that includes cognitive, executive functioning, language, socioemotional, behavioral, and health characteristics that contribute to children’s ability to adapt and thrive in school settings. These performance domains are correlated but typically are assessed and studied as independent indicators of school readiness and predictors of later achievement. Importantly, the guiding definitions of school readiness typically include skills and behaviors that are related to learning processes as wellas learning outcomes, as opposed to the K–12 system, which often only emphasizes student outcomes based on children’s performance on academic achievement tests.
In the area of cognition, school readiness includes both acquired knowledge or skills in a particular content area (such as knowing a certain number of letters) as well as learning/processing skills or how fast children acquire knowledge. In particular, there has been a growing emphasis on executive functioning skills and how these skills interact with other domains to promote learning in preschool classrooms. Executive functioning typically is defined as the set of skills and behaviors required to attain a goal, including working memory, attention control, attention shifting, and response inhibition. For young children, this means being able to resist distractions (e.g., pay attention to a teacher rather than talk with peers), inhibit dominant responses in emotional contexts (e.g., raise hand instead of talking while the teacher is reading a book), and prioritize and sequence information and hold onto it in memory (e.g., plan and carry out the series of steps required to line up for lunch).
In addition, school readiness includes children’s language skills, including their receptive language (i.e., the ability to listen and understand language) and expressive language (i.e., the ability to communicate with others using verbal language). Children’s socioemotional skills are also an important component of school readiness and include behaviors such as cooperation with teachers and peers and developing social relationships, as well as behavior problems, including aggression or poor regulation. There are also a set of skills referred to as approaches to learning, which reflect children’s curiosity, flexibility, attention, persistence, and engagement. The physical health domain includes motor development, such as development of fine and gross motor skills, and healthy behavior practices. Collectively, all of these skills are theorized to affect children’s learning opportunities and their acquisition of new skills and behaviors in the classroom setting.
12. According to the passage, being able to resist distractions is a form of
(A) socioemotional growth.
(B) executive functioning.
(C) behavioral growth.
(D) motor development.
(E) cognitive growth.
13. The author of the passage makes the distinction between the guiding principles of school readiness and those observed by the K–12 system to
(A) emphasize that school readiness regards the process as much as the results.
(B) demonstrate the failings of the K–12 system.
(C) explain why the guiding principles of school readiness are superior to those used at K–12 settings.
(D) emphasize the author’s opinion about the importance of student outcomes.
(E) explain how cognition factors into a child’s degree of success in a school setting.
14. The passage indicates that attention to which one of the following school readiness skills has increased in recent years?
(A) responding accurately on standardized achievement tests
(B) using verbal language to communicate ideas to others
(C) cooperating with peers and managing aggressive behaviors
(D) paying attention to the teacher
(E) ensuring that students consume a healthy breakfast
15. It can be inferred from the passage that children who collaborate successfully with their teachers and other students have strong
(A) motor skills.
(B) receptive language skills.
(C) expressive language skills.
(D) executive functioning skills.
(E) socioemotional skills.
16. Career counselor: Many large international companies have changed their practices regarding international assignments. They are placing much more emphasis on helping spouses of expatriate employees to adjust to the foreign environment. This has reduced premature returns by 67 percent.
Which one of the following is an assumption upon which the career counselor’s argument depends?
(A) Spousal and marital difficulties were formerly responsible for many premature returns from foreign assignments.
(B) When employees are placed in a foreign assignment for a year or less, their families see the assignment as an adventure.
(C) Expatriate employees work long hours and travel a great deal, and their children make new friends at school, but spouses often have no friends and no work to support them while they are abroad.
(D) The majority of international assignments today last for less than a year, but ten years ago, 70 percent of them lasted much longer than one year.
(E) Many companies now offer expatriate spouses language training, career guidance, and assistance in finding homes and schools.
17. Scientists have discovered a gene that controls whether an individual is monogamous. They took a gene from the monogamous prairie vole and implanted it into its more promiscuous relative, the meadow vole. Thereafter, the meadow voles with the new gene became monogamous.
Which one of the following, if true, would provide the most support for the argument’s conclusion?
(A) Studies on humans and other mammals have shown that receptors for the hormone vasopressin play a role in autism, drug addiction, and the formation of romantic attachments.
(B) Prairie voles typically form lifelong partnerships, which scientists have linked to an increased number of receptors for the hormone vasopressin.
(C) Meadow voles live in a harsher environment than prairie voles and cannot afford to pass up opportunities to mate as often as possible.
(D) The scientists used a harmless virus to capture the gene and transfer it into the meadow voles.
(E) The meadow voles that had the prairie vole gene implanted in them were released into and observed in the same habitat in which they had previously lived.
18. Physician: Scottish researchers have developed a test that allows them to predict at what age a woman will experience menopause. The scientists use a model that compares a woman’s ovaries to “average” ovaries to see whether her ovaries are aging faster or more slowly than average. They have discovered that the size of ovaries is directly related to the number of eggs they contain, which in turn is directly related to fertility. This discovery will significantly influence women’s decisions on when to have children.
The physician’s conclusion follows logically if which one of the following is assumed?
(A) Women with smaller ovaries tend to have less success with assisted reproduction techniques, such as in vitro fertilization.
(B) Most women experience menopause around the age of 50, but their fertility starts to decline at the age of 37.
(C) Women who want to have children increasingly seek to delay doing so for many varied reasons.
(D) The test cannot tell women how likely they are to conceive in the years just prior to menopause.
(E) Every woman is born with several million eggs in her ovaries, which formed while she was a fetus; the number of eggs dwindles over her lifetime, until at menopause she has 1,000 or fewer.
19. To earn a graduate equivalency diploma, students must pass tests on subjects taught in high schools, proving that they have mastered them to the degree assumed of high school graduates. It makes sense for students to drop out of high school and earn GEDs. A GED takes much less time to earn than a high school diploma and provides evidence that students have learned everything they would have learned in high school.
Which one of the following, if true, most seriously weakens the argument?
(A) Some GED-prep programs incorporate enrichment activities into their test preparation, such as taking students to art exhibits and theatrical performances.
(B) Most colleges and universities consider a GED equivalent to a high school degree for admission purposes.
(C) Many successful businesspeople dropped out of high school and earned a GED.
(D) Employers assume that high school graduates generally have a much higher level of mastery of academic subjects than those who earn GEDs.
(E) Many GED students are slightly older than high school students, and they often hold jobs in addition to studying to pass the GED tests.
Questions 20–23 refer to the following passage, which is excerpted from Beyond Cybersecurity: Protecting Your Digital Business, by James M. Kaplan, Tucker Bailey, Derek O’Halloran, Alan Marcus, and Chris Rezek (John Wiley & Sons, Inc. 2015).
All business investments require trade-offs between risk and reward. Does the interest rate on a new bond issue adequately compensate for the risk of default? Are the potential revenues from entering a new emerging market greater than the risk that the investments will be confiscated by a new regime? Does the value of oil extracted via deep-water, offshore drilling outweigh the chance of a catastrophic accident? Tough questions must be answered by weighing up the business imperatives against a calculation of the risk — and the greater the risk, the harder it is to make the case for investment.
Technology investments are no different. They, too, have always been a trade-off between risk and return. However, for enterprise technology, increased global connectivity is raising the stakes on both sides of the equation. The commercial rewards from tapping into this connectivity are enormous, but the more tightly we are connected, the more vulnerabilities exist that attackers can exploit and the more damage they can do once inside. Therefore, when a manufacturer invests in a new product life-cycle management system, it is making a bet that the system will not enable the theft of valuable intellectual property. When a retailer invests in mobile commerce, it is betting that cyber-fraud won’t critically damage profitability. When a bank invests in customer analytics, it is betting that the sensitive data it analyzes won’t be stolen by cyber-criminals. The odds on all those bets appear to be shifting away from the institutions and toward cyber-attackers. They could swing decisively their way in the near future given most companies’ siloed and reactive approach to cybersecurity.
Our interviews with business leaders, chief information officers (CIOs), chief technology officers (CTOs), and chief information security officers (CISOs) indicate that concerns about cyber-attacks are already affecting large institutions’ interest in and ability to create value from technology investment and innovation. Potential losses, both direct and indirect, reduce the expected economic benefits of technology investments, as do the high cost and lengthy time frame required to build the defense mechanisms that can protect the organization against a growing range of attackers. In short, the models companies use to protect themselves from cyber-attack are limiting their ability to extract additional value from technology.
Concern about cyber-attacks is already having a noticeable impact on business along three dimensions: lower frontline productivity, fewer resources for information technology (IT) initiatives that create value, and — critically — the slower implementation of technological innovations.
20. The primary purpose of this passage is to
(A) identify gaps in the business world that lead to cybersecurity breaches.
(B) refute the notion that companies are failing to thwart hackers.
(C) discuss how the modern business marketplace is all about risk and reward.
(D) explain how attention to cybersecurity impacts companies’ technological innovation.
(E) demonstrate how today’s hackers are winning the fight against big corporations.
21. According to the passage, all of the following decrease the economic benefits of technological investment EXCEPT
(A) experiencing stolen intellectual property.
(B) realizing indirect losses.
(C) weighing business outcomes and risks.
(D) investing in cybersecurity protection technology.
(E) reacting to cyber-threats only when necessary.
22. When the authors assert that companies take a “siloed and reactive” approach to cybersecurity, they are implying that companies
(A) perform thorough research before implementing programs meant to improve cybersecurity.
(B) combat problems after they have occurred.
(C) have made strides against hackers in the ultimate battle of cybersecurity.
(D) invest too much in cybersecurity.
(E) take unnecessarily large investment risks and disregard the importance of cybersecurity.
23. Which one of the following is an example of intellectual property as mentioned in the second paragraph?
(A) works of art posted to social media
(B) personal information, such as Social Security numbers or banking information
(C) computers and related technological devices
(D) customer and client lists and related contact information
(E) an outline of a streamlined manufacturing process





